- Pillars of Information Security
Information security is the practice of protecting information by maintaining its confidentiality, integrity, and availability. These three principles form the pillars of information security, and they’re often referred to as the CIA triad
- Confidentiality
Confidentiality entails limiting access to data to authorized users and systems. In other words, confidentiality prevents the exposure of information to anyone who is not an intended party.
The concept of confidentiality is closely related to the security best practice of least privilege, which asserts that access to systems or information should only be granted on a need-to-know basis. To enforce the principle of least privilege and maintain confidentiality, you must classify (or categorize) data by its sensitivity level.
- Integrity
Integrity involves maintaining the accuracy, validity, and completeness of information and systems. It ensures that data is not tampered with by anyone other than an authorized party for an authorized purpose.
A checksum is a value derived from a piece of data that uniquely identifies that data and is used to detect changes that may have been introduced during storage or transmission. Checksums are generated based on cryptographic hashing algorithms and help you validate the integrity of data.
- Availability
Availability is all about ensuring that authorized users can access required systems and data when and where they need it
One of the most common attacks on availability is Distributed Denial of Service, or DDoS, which is a coordinated attack by multiple compromised machines disrupting a system’s availability. Another common and rapidly growing attack on availability is ransomware, which involves an attacker blocking a system or data owners from accessing their systems and data until a sum of money is paid.
- Security controls
You know all about confidentiality, integrity, and availability — that’s great! Now, how do you enforce those concepts in your systems? Security control is the specific mechanism or measures implemented to safeguard systems or assets against potential threats and vulnerabilities — said another way, security controls protect the confidentiality, integrity, and availability of your systems and data.
Security controls can be categorized in a couple of ways: by their type and by their function.
Types of security control include:
- Technical controls use technology (shocking, I know!) to protect information systems and data. Things like firewalls, data loss prevention (DLP) systems, and encryption fall under this category.
- Physical controls involve the use of physical measures to protect an organization’s assets. This can include things like doors, gates, surveillance cameras, and physical disposal of sensitive information (including things like shredding and degaussing).
- Administrative controls include the set of policies, procedures, guidelines, and practices that govern the protection of systems and data. This can be anything from incident response plans (see later in this chapter) to security awareness training.
Functions of security controls include:
- Preventative controls keep negative security events from happening. This includes things like security awareness training, locked doors, and encryption.
- Detective controls identify negative security events when they do happen. Examples of detective controls include log monitoring and video surveillance.
- Corrective controls fix or reduce damages associated with a negative security event and may include measures to prevent the same negative event from happening again. Backups and system recovery features are the most common examples of corrective controls.
- Threats, Vulnerabilities, and Risks
Threats, vulnerabilities, and risks are interrelated terms describing things that may compromise the pillars of information security for given system or an asset (the thing you’re protecting).
- Threats
A threat is anything capable of intentionally or accidentally compromising an asset’s security. Some examples of common threats include:
- Natural disasters: Earthquakes, hurricanes, floods, and fires can cause physical damage to critical infrastructure, leading to loss of connectivity, power outages, or even destruction of systems.
- Malware: Malicious software such as viruses, worms, and ransomware can infect systems, steal data, or disrupt normal business operations.
- Phishing attacks: Deceptive emails, messages, or websites designed to trick individuals into revealing sensitive information like passwords, credit card numbers, or personal data.
- Denial of service (DOS) attacks: Deliberate attempts to overload a network, server, or website with excessive traffic, making it unavailable to legitimate users.
- Vulnerabilities
A vulnerability is a weakness or gap existing within a system; it’s something that, if not taken care of, may be exploited to compromise an asset’s confidentiality, integrity, or availability. Examples of vulnerabilities include:
- Unpatched software: Failure to install updates or patches for operating systems, applications, or firmware, leaving security vulnerabilities open to exploitation.
- Lack of environmental protection: Missing or faulty fire suppression systems or other physical protections, leaving infrastructure vulnerable to natural disasters and other environmental threats.
- Insecure passwords: The use of commonly used or otherwise insecure passwords, makes it easier for attackers to gain unauthorized access to accounts or systems.
- Untrained employees: Lack of security awareness training for employees and system users, leaving them susceptible to phishing attacks.
Threats are pretty harmless without an associated vulnerability, and vice versa. A good fire detection and suppression system gives your data centre a fighting chance, just like (you hope) thorough security awareness training for your organization’s employees will neutralize the threat of an employee clicking on a link in a phishing email.
- Risks
Risk is used to define the potential for damage or loss of an asset. Risk = Threat x Vulnerability. This simple equation is the cornerstone of risk management.
Some examples of risks include:
» A fire wipes out your data centre, making service unavailable for five days.
» A hacker steals half of your customer’s credit card numbers, causing significant reputational damage to your company.
» An attacker gains root privilege through a phishing email and steals your agency’s Top Secret defence intelligence
- Identity and Access Management (IAM)
IAM consists of four key elements: identification, authentication, authorization, and accountability.
- Identification is the act of establishing who (or what) someone (or something) is. In computing, identification is the process by which you associate an entity (i.e., a system or user) with a unique identity or name, such as a username or email address.
- Authentication takes identification a step further and validates a user’s identity. During authentication, you answer the question “Are you who you say you are?” before authorizing access to a system.
Authenticators generally fit into one of three factors (or methods):
- Something you know: Passwords and PINs (Personal Identification Numbers) fall into this category.
- Something you have: Security tokens and smart cards are examples of this factor.
- Something you are: Examples of this factor include fingerprints, iris scans, voice analysis, and other biometric methods
- Authorization is the process of granting access to a user based on their authenticated identity and the policies you’ve set for them.
- Accountability involves assigning and holding an entity responsible for its actions within an information system. Accountability requires establishing unique user identities, enforcing strong authentication, and maintaining thorough logs to track user actions
- Encryption and decryption
Encryption is the process of using an algorithm (or cipher) to convert plaintext (or the original information) into ciphertext. The ciphertext is unreadable unless it goes through the reverse process, known as decryption, which then allows an authorized party to convert the ciphertext back to its original form using the appropriate encryption key(s).
Types of encryption
Encryption can either be symmetric-key or asymmetric-key. The two encryption types function very differently and are generally used for different applications.
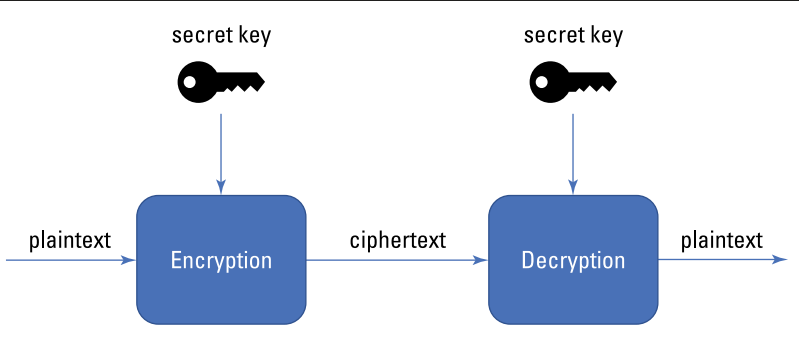
- Symmetric-key encryption (sometimes referred to as secret-key encryption) uses the same key (called a secret key) for both encryption and decryption (see Figure). Using a single key means the party encrypting the information must give that key to the recipient before they can decrypt the information. The secret key is typically sent to the intended recipient as a message separate from the ciphertext. Symmetric-key encryption is simple, fast, and relatively cheap.
A notable drawback of symmetric-key encryption is it requires a secure channel for the initial key exchange between the encrypting party and the recipient. If your secret key is compromised, the encrypted information is as good posted on a billboard.
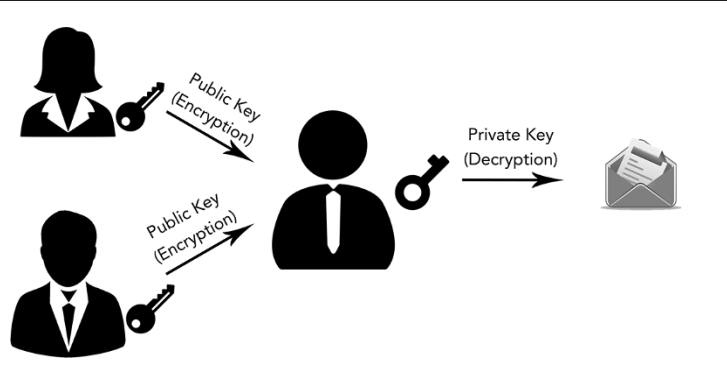
- Asymmetric-key encryption (more commonly known as public-key encryption) operates by using two keys — one public and one private. The public key, as you might guess, is made publicly available for anyone to encrypt messages. The private key remains a secret of the owner and is required to decrypt messages that come from anyone else (see Figure). Although public-key encryption is typically slower than its counterpart, it removes the need to secretly distribute keys and also has some very important uses
Common uses of encryption: Data Protection(in-Rest and in-transit), Authentication and Authorization, Network Security(TLS), Digital Signature, VPN, Crypto-Shredding, etc.
- Importance of Business Continuity and Disaster Recovery
Business continuity (BC) refers to the policies, procedures, and tools you put in place to ensure critical business functions continue during and after a disaster or crisis. The goal of business continuity is to allow essential personnel the ability to access important systems and data until the crisis is resolved.
DR is the part of BC focused on restoring full operation of and access to hardware, software, and data as quickly as possible after a disaster.
Business continuity broadly focuses on the procedures and systems you have in place to keep a business up and running during and after a disaster. Disaster recovery more narrowly focuses on getting your systems and data back after a crisis hits.
You need to be aware of a couple important related metrics:
» Recovery Time Objective (RTO) is the amount of time within which business processes must be restored in order to avoid significant consequences associated with the disaster. In other words, RTO answers the question “How much time can pass before an outage or disruption has unacceptably affected my business?”
» Recovery Point Objective (RPO) is the maximum amount of data loss that’s tolerable to your organization. It answers the question “How much data can I lose before my business is unacceptably impacted by a disaster?” RPO plays an important role in determining frequency of backups.
#> echo "Thank you :)"